Pretty Good Privacy (PGP) encryption is widely used to secure sensitive information and maintain data privacy. If you’re looking to decrypt PGP files using an Azure Function App, you’re in the right place.

Table of Content
- Table of Content
- Objective of this article :
- Introduction
- Understanding PGP Encryption
- Setting Up Azure Function
- GitHub Repository for PGP File Decryption Azure Function project
- Scenario: Decrypting Sensitive XML Data
- Calling Your Azure Function from Azure Logic Apps
Objective of this article :
In this tutorial, we’ll guide you through the process of decrypting PGP files using Azure Function App. With Azure Function App, you can easily automate decryption processes by executing your code in a serverless environment.
Throughout this article, we will provide step-by-step guidance on setting up an Azure Function environment and writing .NET code for PGP decryption. Let’s dive in!
Introduction
Ensuring the security of our data is important. To achieve this, one effective method is by utilizing PGP encryption, a reliable and trusted approach to safeguarding information. In this article, we will delve into the fundamentals of PGP encryption and provide you with a step-by-step guide on how to effortlessly decrypt PGP files using Azure Function. But before we proceed, let’s start with the basics.
PGP, which stands for Pretty Good Privacy, and it does just that :). It operates like a lock and key system, where your data acts as the lock that can only be opened with the correct key in the form of a secret code. Using Azure Function, we’ll create a secure environment to decrypt files encrypted with PGP. Our goal is to simplify the PGP process and guide you through setting up Azure Function so that you can effortlessly unlock PGP-encrypted files by the end of this article.
Understanding PGP Encryption
What is PGP Encryption?
PGP (Pretty Good Privacy) is an encryption method widely utilized to safeguard digital communications and safeguard sensitive information. It plays a crucial role in the cybersecurity area.
Why it’s important
Protecting sensitive data is absolutely essential. PGP encryption is a vital tool in this effort. Let’s explore further why it is so critical:
- Data Privacy : PGP encryption ensures data privacy. Whether you’re sending confidential emails, storing sensitive documents, or sharing critical information, you need assurance that only the intended recipient can access that data. PGP provides precisely that, acting as a digital vault protecting your information from unauthorized access.
- Compliance requirements : Various industries and sectors have strict compliance regulations that mandate data protection. For instance, in the healthcare or Gazes field, HIPAA in the United States or GDPR in the European Union require the encryption of data to avoid hefty penalties. PGP encryption helps organizations adhere to these regulations seamlessly.
- Secured data integration : For businesses that rely on Microsoft Dynamics 365 Finance and Operations to manage their financial and operational data, data import is a routine operation. Often, this data comes from external systems or partners. PGP encryption ensures that data remains secure during import. Even if it originates from external sources, it’s protected throughout the transfer process. This is particularly crucial when dealing with financial data, as errors or breaches can have far-reaching consequences.
Key concepts
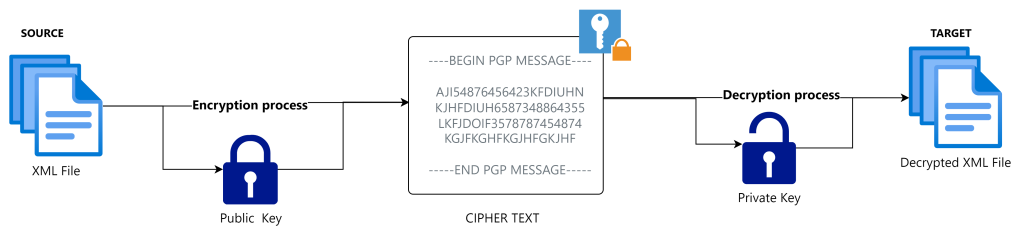
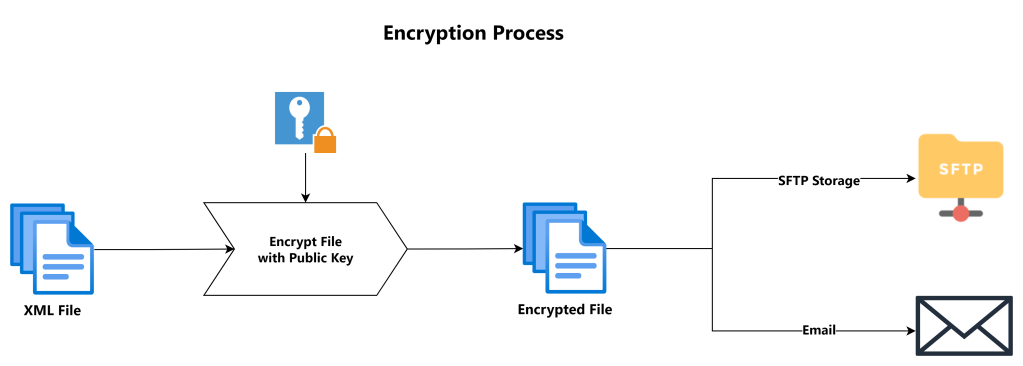
- Encryption : PGP converts plain text (your message / file / email …) into ciphertext (an unreadable format) using complex mathematical algorithms. This ensures the message is secure during transmission or storage.
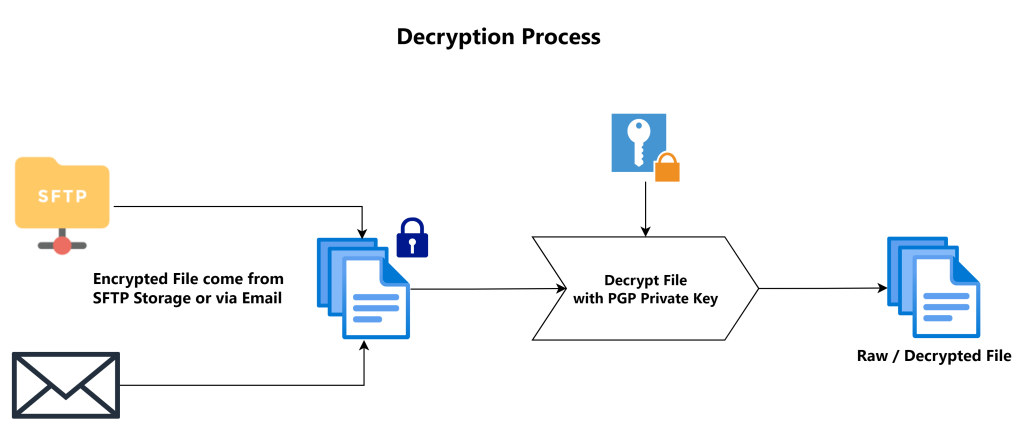
- Decryption : The recipient uses a private key (kept secret) to transform the ciphertext back into plain text, making the message readable.
- Key Pair : PGP operates on a pair of keys – a public key for encryption (shared with anyone) and a private key for decryption (kept secret by the owner).
What Is The Mechanism behind PGP’s Functionality?
PGP encryption functions via a process that merges symmetric-key and asymmetric-key cryptography.
- Private and Public Key Pair: PGP employs twin keys – one public key plus one private key.
- Public Key Encryption: Whenever an individual intends to deliver an encrypted communication towards you, they adopt your public key. This specific key has the ability to solely encrypt data as it is incapable of decrypting it.
- Symmetric-Key Encryption: PGP streamlines procedures by generating an ephemeral, random symmetric key
- Message Encryption: The sender uses the symmetric key for encrypting their communication
- Sending: They forward you both the codified message along with the concealed symmetric key
- Decryption: Once you receive this encrypted note, deploy your private key for decrypting that hidden symmetric key plus use the latter for decoding the actual message
Real-World Scenarios
PGP encryption matters because it’s a shield for sensitive data in our digital world.
- Secure Email Communication : PGP is commonly used to encrypt email messages, ensuring that only the intended recipient can read the content.
- Protecting Financial Data : In the finance industry, PGP encryption secures sensitive financial data during transmission.
- Medical Records : Healthcare providers use PGP to protect electronic health records (EHRs) and ensure patient privacy.
- File Storage : PGP can encrypt files stored on servers or cloud platforms, adding an extra layer of security.
- Legal Documents : Law firms use PGP to safeguard confidential legal documents.
Setting Up Azure Function
Azure Function is an event-driven, serverless compute platform that helps you develop more efficiently using the programming language of your choice. Focus on core business logic with the highest level of hardware abstraction.
Azure Function will be our gateway to efficient and automated data decryption processing, through a serverless function. In this section, we’ll guide you through the process of setting up your Azure Function environment and .NET Runtime code of the Azure Function App.
Creating Your Azure Function Environment
Azure Function is part of Microsoft Azure, a comprehensive cloud computing platform offering a diverse range of services. It stands as a prime example of serverless computing.
The process of creating your Azure Function environment can be undertaken through two complementary avenues: the Visual Studio and Azure Portal.
Prepare your Visual Studio Azure Function Project
Project configuration
Azure Function development can be carried out using Visual Studio. This approach is often favored by developers who appreciate a more comprehensive development experience, but also to created the customized business logic and the associated Git Repository to manage your code changes for CI/CD.
- Project Template : Create a new project, for « Azure Functions » in the search bar. Select the « Azure Functions » template and click « Next. »
- Configure Your Project : In the project configuration window, provide the necessary information:
- Version : Choose the version of .NET Core that aligns with your requirements. Ensure it’s compatible with Azure Functions.
- Note : In your Azure Function .NET code, you’ll be leveraging specific .NET libraries to accomplish tasks like PGP decryption. It’s imperative to note that the versions of these .NET libraries must align with the Azure Function runtime version you’re using. Additionally, keeping these libraries up-to-date through periodic maintenance is essential for the reliability and security of your Azure Function.
- Authentication : Depending on your project’s requirements, you can configure authentication settings. For this PGP decryption Azure Function, you may not need authentication, but consider your security needs. Here we will use the « Function » acces right, which means that you have to present the function key in requests to access your function endpoint in Azure.
- Note : you can choose « Function » for authorization, but for production scenarios, you may want to implement more robust authentication.
- Version : Choose the version of .NET Core that aligns with your requirements. Ensure it’s compatible with Azure Functions.
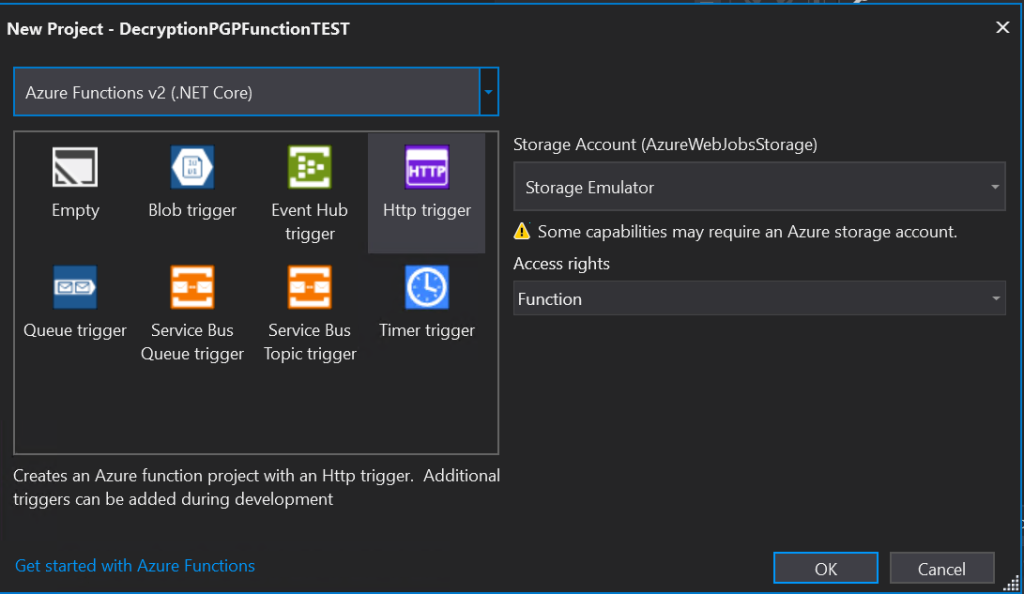
- Select a Template : Visual Studio will prompt you to select a template for your Azure Function. Given our objective of PGP decryption, you can choose the « HTTP trigger » template as a starting point. This template is suitable for functions that respond to HTTP requests, making it ideal for decryption tasks.
Project Structure
Visual Studio will create the Azure Function project structure for you. You’ll find a file named Function1.cs in the « Functions » folder. This file contains the code for your HTTP-triggered function.
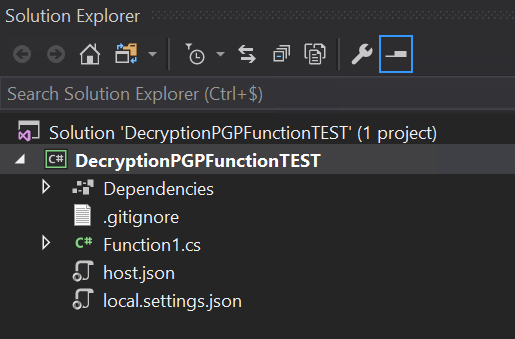
- Writing the PGP Decryption Logic: In the generated function file, you can write the C# code for decrypting PGP-encrypted files. You’ll need the appropriate libraries and keys to perform decryption securely.
Using .NET Libraries in Your Azure Function
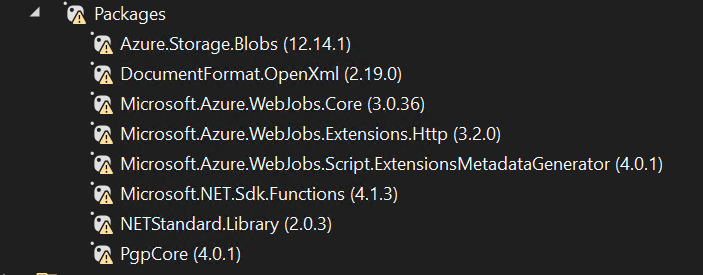
In your Azure Function .NET code, you’ll be leveraging specific .NET libraries to accomplish tasks like PGP decryption. It’s imperative to note that the versions of these .NET libraries must align with the Azure Function runtime version you’re using. Additionally, keeping these libraries up-to-date through periodic maintenance is essential for the reliability and security of your Azure Function. in the next section we will discover the list of .NET References to be used.
Leveraging Azure Storage Blobs, PGP Core, Azure WebJobs .NET References in your Azure Function
In your Azure Function, you’ll harness the capabilities of Azure Storage Blobs, PGP Core, and Azure WebJobs .NET references to create a robust solution for decrypting PGP-encrypted files. Here’s a brief overview of each component’s role :
Azure Storage Blobs .NET Library :
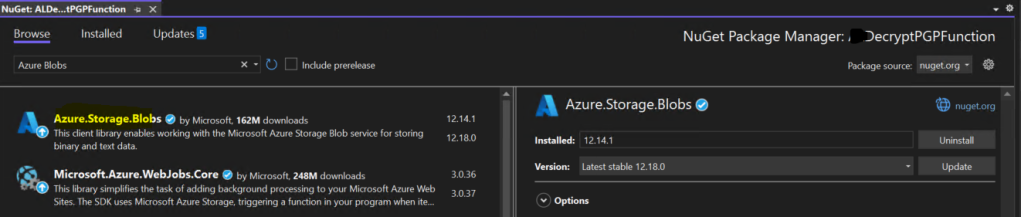
- Role: Azure Storage Blobs serve as your secure data repository. You can store the PGP-encrypted files in Azure Blob Storage, ensuring that they are readily accessible to your Azure Function.
- Advantages: Azure Blob Storage offers scalability, redundancy, and security for your data. It’s an ideal choice for storing sensitive files like PGP-encrypted data.
PGP Core .NET Library :
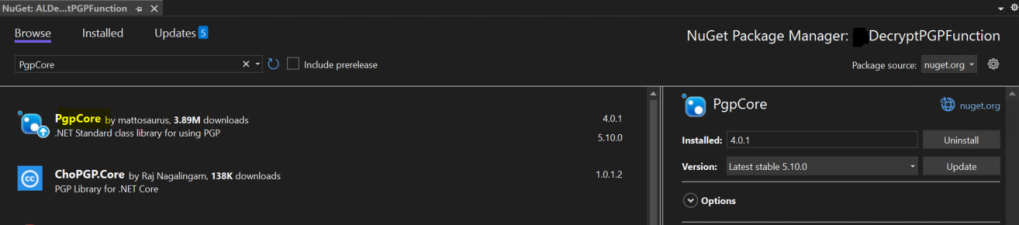
- Role: PGP Core .NET references are essential for implementing PGP decryption within your Azure Function. These libraries provide the necessary cryptographic functions to unlock the PGP-encrypted files.
- Advantages: PGP Core libraries simplify the decryption process, ensuring that your data remains confidential and secure. They abstract the complex cryptographic operations, making it easier to handle PGP encryption within your function.
Azure WebJobs .NET Library:
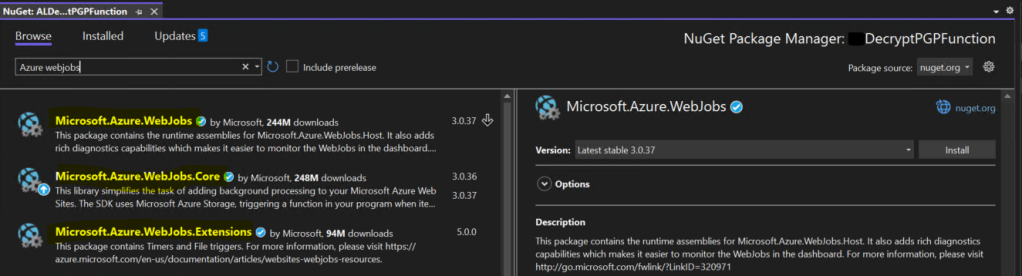
- Role: Azure WebJobs is an integral part of Azure Functions, enabling you to schedule and automate tasks. In your scenario, you can use Azure WebJobs to trigger your Azure Function at predefined intervals or in response to specific events, such as the arrival of new PGP-encrypted files in Azure Blob Storage.
- Advantages: Azure WebJobs provide automation capabilities, ensuring that your PGP decryption process is executed precisely when needed. This automation reduces manual intervention and streamlines your data handling workflow.
Best Practices for Version Compatibility
When working with Azure Functions and .NET libraries, adhering to best practices for version compatibility is essential. This ensures that your project remains stable and secure. Here are some recommendations:
- Always verify that the version of .NET Core you’re using in your Azure Function is compatible with the Azure Function runtime. Refer to Azure documentation or official resources for compatibility information.
- Regularly update the .NET libraries and dependencies used in your project to the latest stable versions. This helps ensure that you have access to the latest features, performance improvements, and security updates.
- Implement continuous integration (CI) and continuous testing practices to automatically verify that your Azure Function works as expected with the selected library versions, we will have a next article about how to create CI/CD build and release pipeline for Azunre Function App.
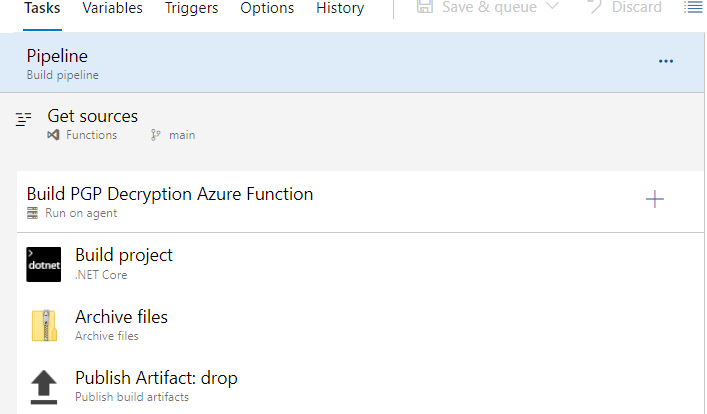
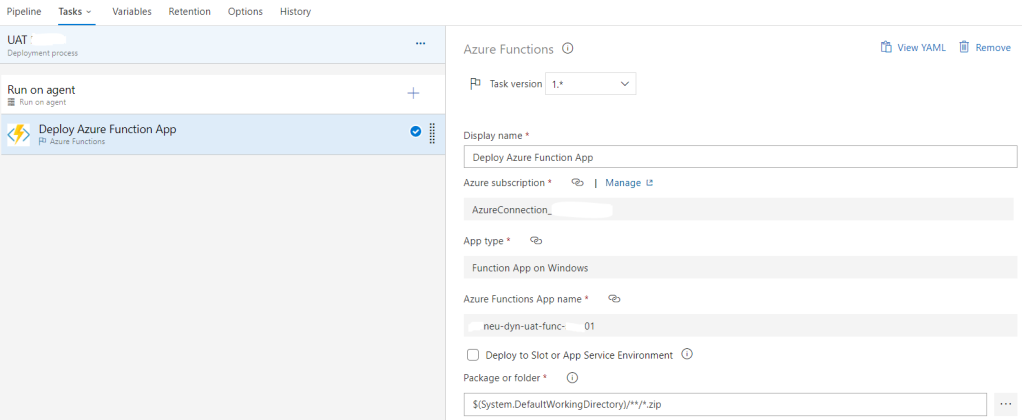
Publish to Azure
Once your function is tested and ready, you can publish it to Azure directly from Visual Studio. Visual Studio streamlines the deployment process, making it convenient to deploy your function to the Azure cloud.
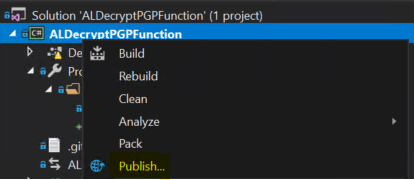
Create a Publish Profile
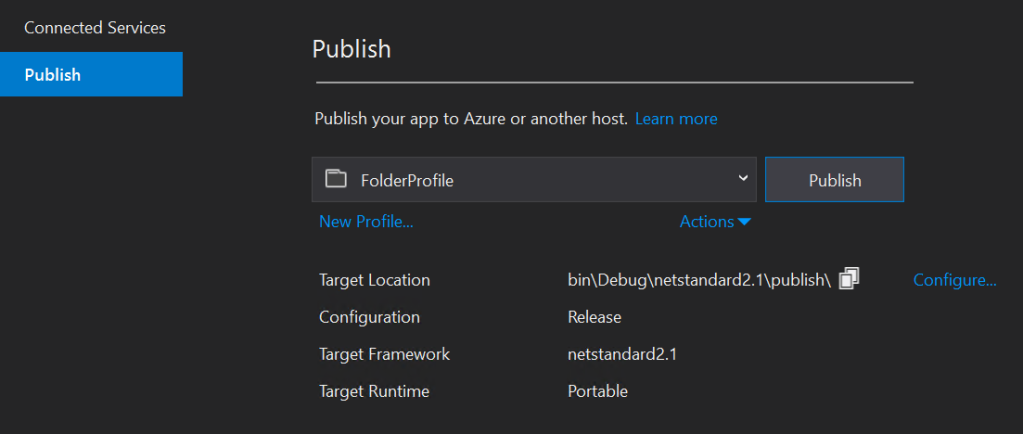
In Visual Studio, a publish profile in an Azure Function project is a configuration file that contains settings and information necessary to publish or deploy your Azure Function to an Azure App Service or another hosting environment. Publish profiles simplify the deployment process by storing deployment-specific details, such as target Azure Function App settings, deployment credentials, and other deployment-related configurations.
GitHub Repository for PGP File Decryption Azure Function project
In the spirit of open-source collaboration, i have made the entire Azure Function project, complete with the PGP decryption logic, available on GitHub. This repository serves as a central hub for the project’s development, documentation, and community engagement.
Access the Repository:
You can find the project on GitHub by visiting AzurePGPDecryption
What you’ll Find:
- Code: Explore the codebase to gain insights into the PGP decryption process within the Azure Function. You’ll find detailed comments and explanations to help you understand and customize the solution for your specific needs.
- Documentation: We’ve included comprehensive documentation to guide you through setting up and configuring the Azure Function, using Azure Blob Storage and PGP Core .NET references, and scheduling tasks with Azure WebJobs.
The repository hosts a .NET Azure Function that enables the decryption of PGP files stored in Azure Blob Storage. The function accepts three parameters to perform the decryption:
- PGP Private Key: The private key used for decrypting the PGP file.
- Encrypted File: The path to the encrypted PGP file stored in Azure Blob Storage.
- Output File: The file path where the decrypted content will be saved.
Here is the principal classes :
Decryption Class
This repository contains a C# class named « Decryption » that represents an Azure Function for decrypting PGP files. The function is triggered via an HTTP request and performs the decryption process using the provided parameters.
Azure File Information Class
« AzureFileInfo » represents the file information required for accessing and processing files stored in Azure Blob Storage. The class provides properties for the Azure Blob Storage connection string, blob container name, and blob name.
Decryption Controller Class
« EncryptionDecryptionController » serves as the controller for handling encryption and decryption operations on PGP files. The class utilizes the PgpCore library and Azure.Storage.Blobs.Specialized namespace for file processing and Azure Blob Storage integration.
Decryption Request Class
« EncryptionDecryptionRequest » represents the request parameters for encryption or decryption operations on PGP files. The class includes properties for input file information, output file information, encryption/decryption key file information, passphrase, and an option for enabling armor mode.
Scenario: Decrypting Sensitive XML Data
In this section, we’ll explore a real-world scenario that demonstrates the importance of securely managing legal documents, employee metadata, and sensitive bank account data using your Azure Function and Azure Blob Storage. This scenario illustrates how your solution effectively addresses common business needs.
The Business Challenge
Context: Imagine you manage a legal department within a large corporation. Your department deals with a multitude of legal documents, including contracts, agreements, and sensitive employee information, such as metadata and bank account details.
Challenge: Ensuring the security and accessibility of these documents and data is paramount. Legal documents must be stored securely, and employee metadata and banking information require strict privacy and compliance measures.
Azure Blob Storage Containers
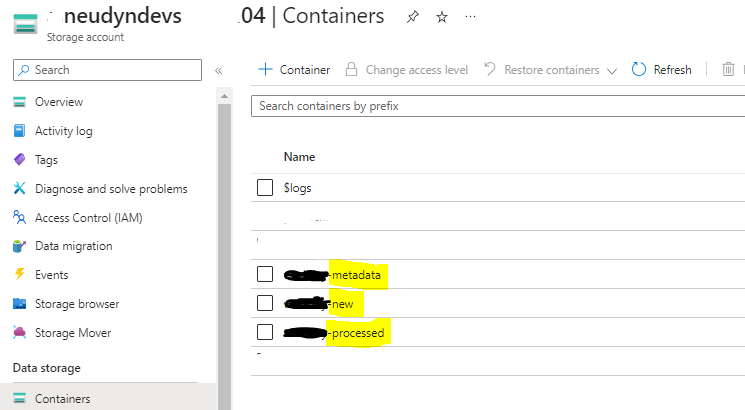
- Encrypted Container « New »: This container serves as a secure repository for storing encrypted legal documents and employee data files. all encrypted files they are placed here.
- Decrypted Container « Processed »: Stores the decrypted legal documents. The Azure Function securely deposits these files here.
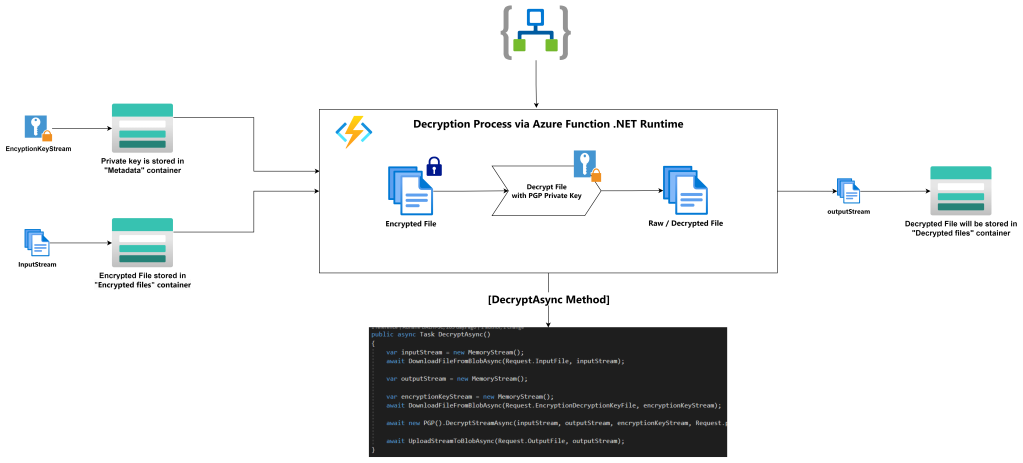
- Private Key Metadata Container « Metadata »: Here you store the essential private key metadata required for decryption. This metadata includes information about the specific private keys used for decryption, key rotation schedules, and access controls.
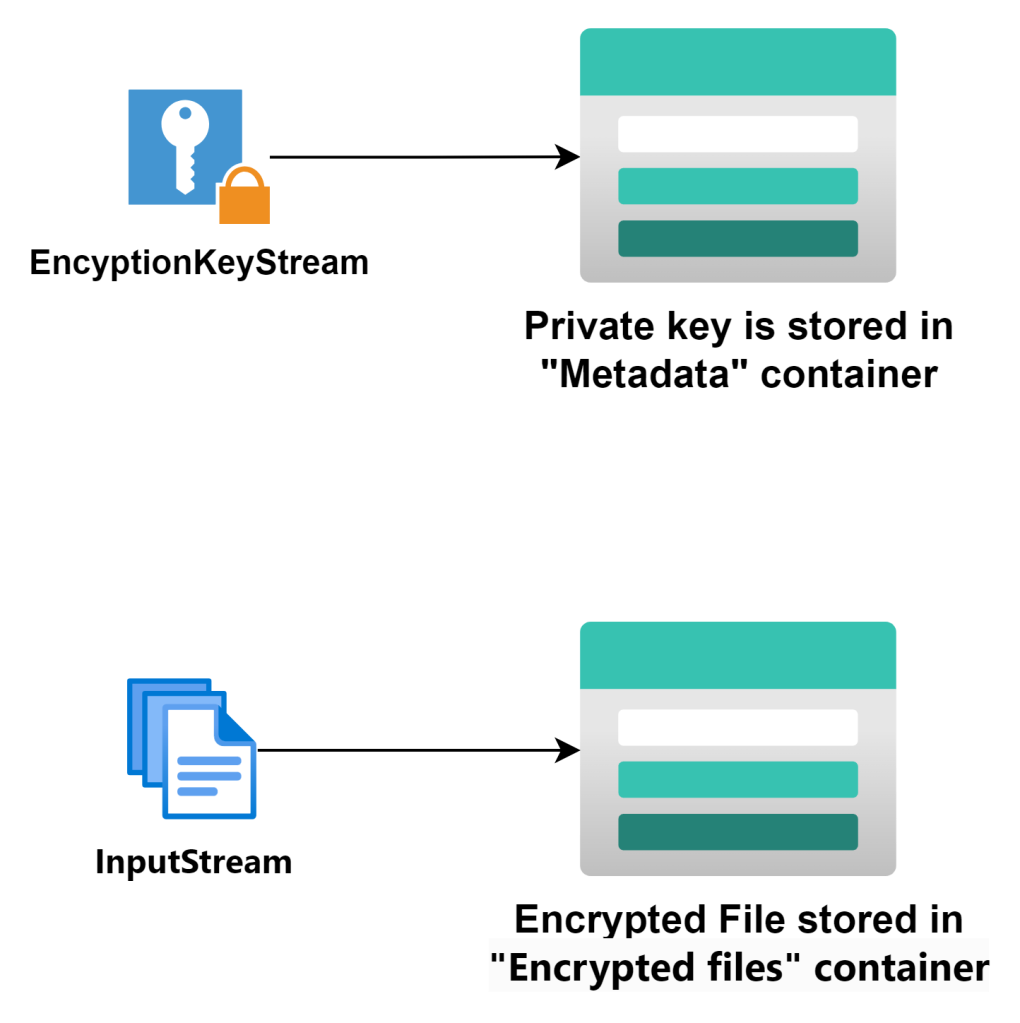
Decryption Workflow
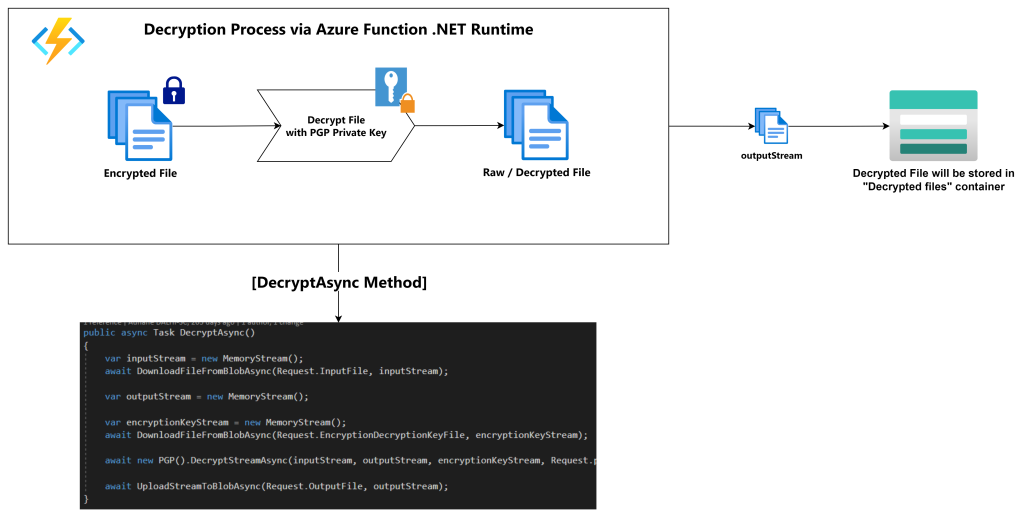
- Secure Key Retrieval: It retrieves the necessary private key metadata from the « Private Key Metadata Container » to ensure that decryption is performed securely.
- PGP Decryption: Leveraging PGP Core .NET references, the Azure Function decrypts the files, transforming them from encrypted data into accessible, plaintext documents.
- Storage in « Decrypted Container – Processed »: The decrypted documents and data are securely stored in the Decrypted Files Container within Azure Blob Storage. This ensures easy and secure access for authorized personnel when needed.
Calling Your Azure Function from Azure Logic Apps
Our Azure Function, designed for PGP decryption and secure data processing, can seamlessly integrate with Azure Logic Apps to create powerful workflows and automation scenarios.
Decryption Input Testing
When calling your Azure Function, it’s crucial to understand the expected input. Here’s what you’ll provide when triggering the function via Postman or Via Azure Logic Apps or any other system, here is the call input parameters.

- EncryptionDecryptionKeyFile: This section specifies the details required to access the private PGP key used for decryption.
- BlobContainerName: It identifies the name of the Azure Blob Storage container where the private PGP key file is located. In this case, it’s « metadata. »
- BlobName: This indicates the specific name of the PGP key file within the « metadata » container. The file is named « PrivatePGPKEY.asc. »
- ConnectionString: This connection string provides access to the Azure Blob Storage account. It includes the necessary security credentials.
- InputFile: This section defines the information needed to access the encrypted XML file that you want to decrypt.
- BlobContainerName: Specifies the name of the Azure Blob Storage container where the encrypted XML file is stored. Here, it’s « new. »
- BlobName: Indicates the specific name of the encrypted XML file within the « new » container.
- ConnectionString: This connection string grants access to the Azure Blob Storage account . It includes the required security credentials.
- OutputFile: This section outlines the details for storing the decrypted XML file once the decryption process is complete.
- BlobContainerName: Specifies the name of the Azure Blob Storage container where the decrypted XML file will be placed. In this case, it’s « processed. »
- BlobName: Indicates the specific name for the decrypted XML file within the « processed » container.
- ConnectionString: This connection string provides access to the Azure Blob Storage account . It includes the necessary security credentials.
- passPhrase: This parameter likely represents a passphrase or password required for the PGP decryption process. In this case, it’s set to « TEST. »
Benefits of Integration
- Automation: Azure Logic Apps provide low-code approach to automation. This integration allows you to automate complex business processes, reducing manual intervention.
- Data Flow: The integration ensures a smooth flow of data from your trigger event to decryption and any subsequent actions. This enables efficient data processing.
- Scalability: Both Azure Logic Apps and Azure Functions can scale dynamically to handle increased workloads as your business grows.
- End-to-End Workflow: By combining Azure Functions and Azure Logic Apps, you can create end-to-end workflows that encompass data ingestion, decryption, and integration, ensuring seamless data processing.